Detect Hacking
We have a broad range of methods to detect hacks including common library hacks, cross site scripting, SQL injection and fake referrers.
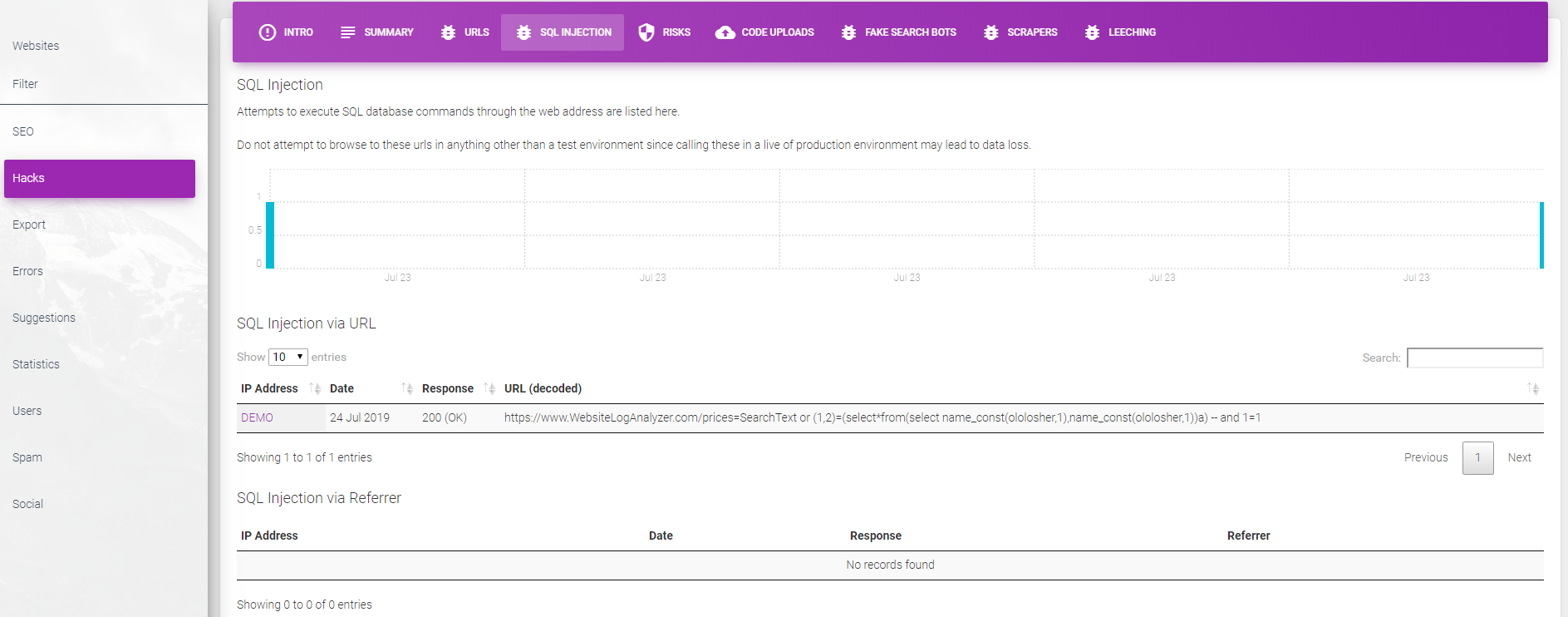
SQL Injection has been around a long time. You may think it does not affect you but hackers are coming up with new ways of getting access to your database. Along with many of the url methods we detect, we also look at the user agent and referrer data being sent by a visitor to see if it contains a malicious payload. If these details are being recorded or considered by your website (or perhaps some third party library it uses) you could be vulnerable.
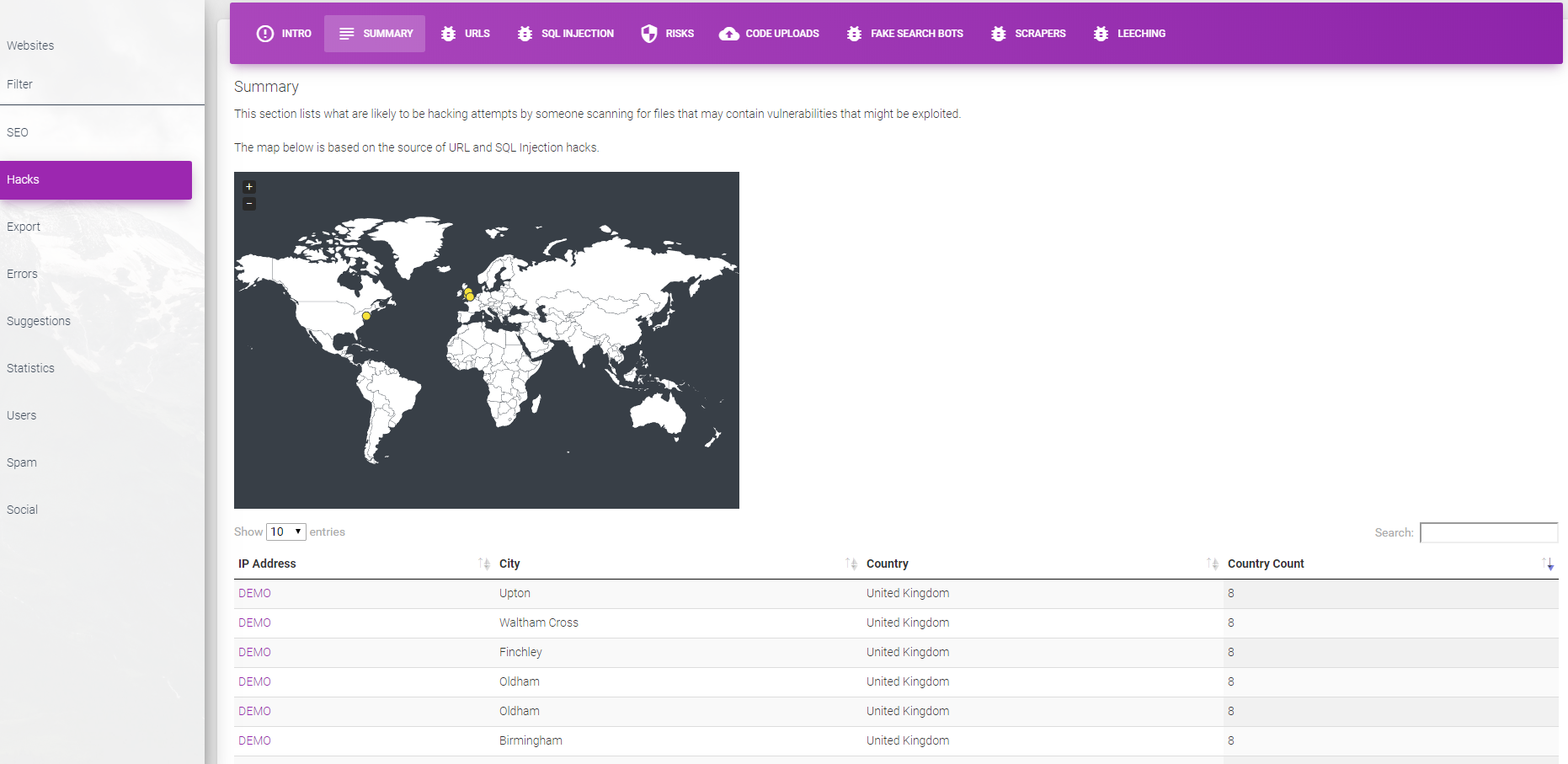
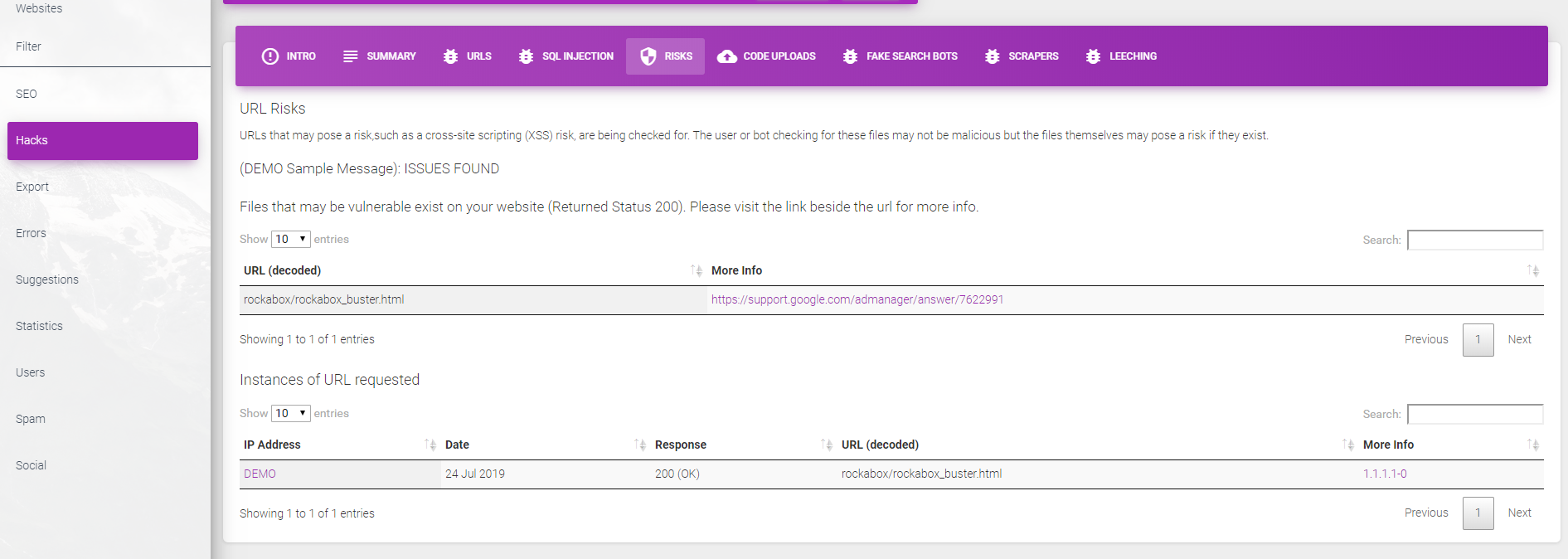
We maintain a large database of urls and attack methods used by hackers and can highlight users attempting to hijack your website. This database is constantly improving and growing.
Our code uploads section can show any instances that a user has tried to upload potentially malicious code to your webserver.
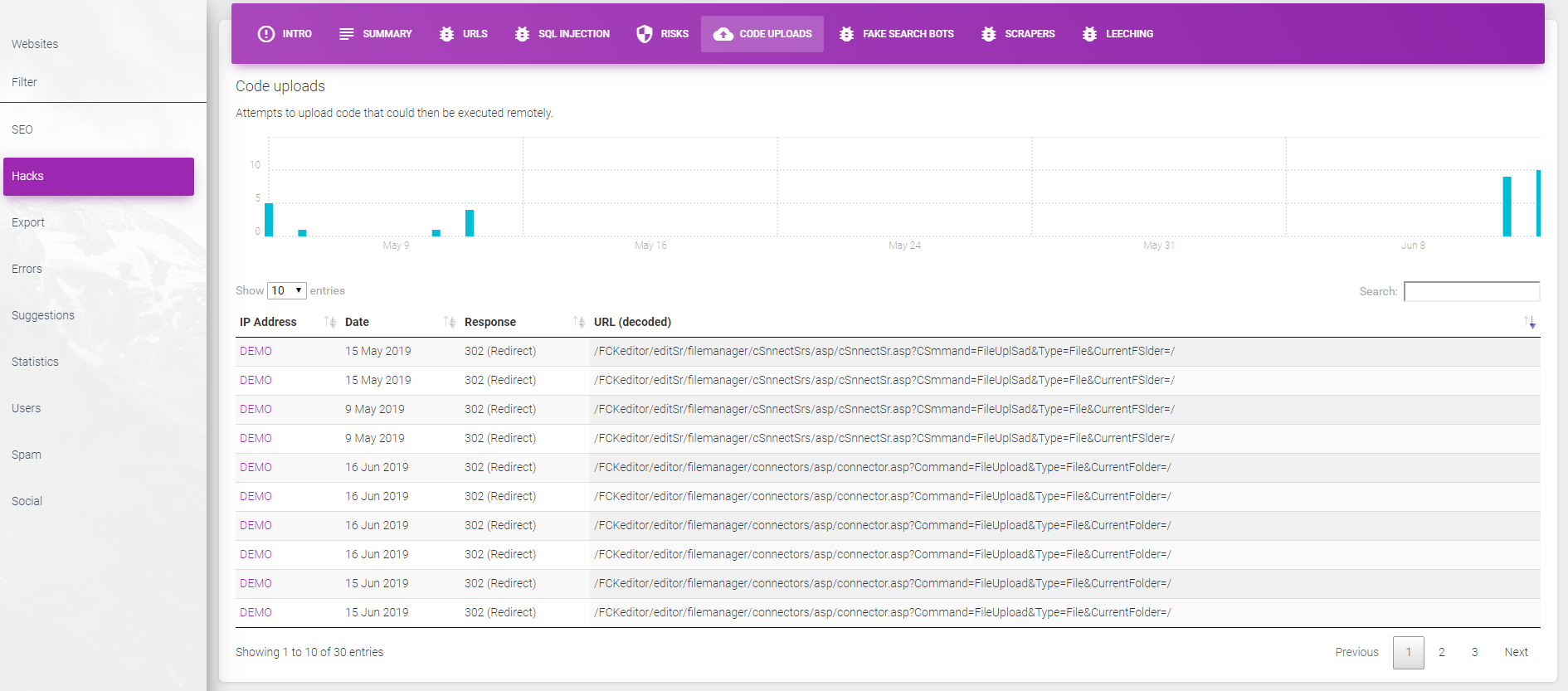
We can also detect bots looking to exploit issues with common libraries. For example, editors and image uploaders might be exploited by hackers to upload malicious code to your webserver.